Usuario: TELMEX
Contraseña: WEP Key default del equipo.
A partir del SSID se puede obtener las posibles WEP Key.
Hemos generado un script (generarrainbowtable.py) que nos permite generar una rainbow table con el SSID y WEP Key correspondientes de 3 OUI de Huawei (001E10, 002568 y 6416F0) [Cabe destacar que esto no hubiera sido posible sin el trabajo de: hochoa@websec.mx - http://websec.mx]
Al obtener el prefijo del SSID lo introducimos al script “generarlistaposibleswep.py” que consulta la base de datos previamente generada y nos escribe el archivo “words.txt” con una lista de 768 posibles WEP Keys el cual se puede utilizar con herramientas como Brutus para realizar un ataque diccionario.
Se obtienen 768 posibles WEP Keys porque en cada OUI se repite el mismo SSID 256 veces, dando así 256 posibilidades de WEP Keys, como hemos procesado 3 OUI distintos 256 * 3 = 768
Ejemplo del ataque:
Para obtener el SSID de un modem remoto por medio de la interfaz web sin estar autenticado utilizaremos la vulnerabilidad “HUAWEI ECHOLIFE HG520c Revelación de Información” publicada por HKM que consiste en abrir la página:
http://<ip remota>/Listadeparametros.html
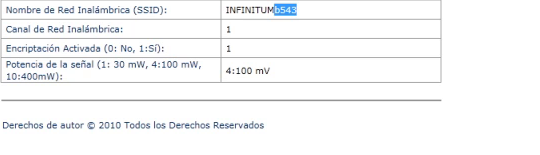
Introducimos el SSID obtenido a generarposibleswepkey.py

Configuramos Brutus con esta lista de contraseñas y con el usuario “TELMEX”.

Descargas:
Generarrainbowtable.py
Generarlistaposibleswep.py
Rainbowtable generada:
Part 1
Part 2
Part 3
Part 4
Part 5
